
Safekeeping the keys to digital assets is a critical issue in today’s digital security. Especially as cryptocurrencies, online accounts and digital identities grow more and more prevalent here in our real world, it becomes an integral part of our daily lives to ensure their strong protection. The following article will cover the basic strategies and techniques to ensure that your trust in the world of digital financial transactions remains unwavering, so that you can store ypur keys as securely as possible.

Hardware / cold wallets
These represent one of the most reliable means for secure storage of crypto and private keys. Such physical devices provide a high level of protection against hackers and malware. Let’s delve into how they work and why they gain traction among investors and common users.
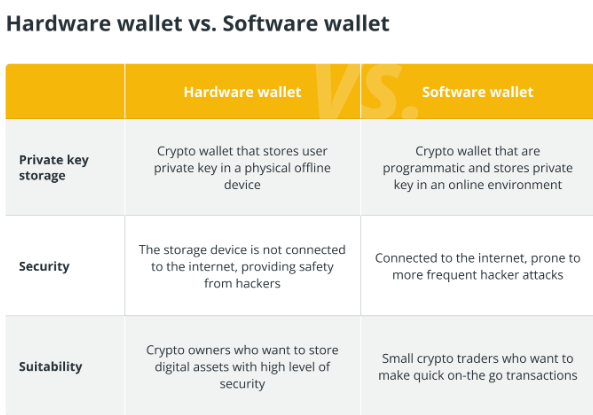
Cold wallets are of a small size which are designed with a single primary purpose – specifically, to provide ultimate security. They act as isolated vaults kept separate from the internet and external threats. Here’s why they’re so trustworthy:
- Offline crypto storage: Hardware wallets operate even out of range. What this means is that they are never connected to the internet unless you deliberately decide to perform a transaction. This makes it all but impossible for hackers to reach your assets via the Web.
- Encryption: Private keys and all related data are stored on hardware wallets in encrypted form. You can’t let attackers access your assets without your seed phrase, even if the device is stolen.
- Physical security: it is common for such wallets to offer physical security measures such as PINs and even biometric identity verification. This extra layer of protection ensures that only you have access to your assets.
- Recovery: If your hardware wallet is lost or damaged, you can always restore access to your assets using the recovery phrase. This provides assurance that your digital affluence will remain safe and secure.

As an alternative to cold wallets, you can use a piece of paper. You can either type somewhere your security key or write it manually. Once this is done, you can fold the paper into an envelope and put it away in a residential safe or safe deposit box. However, be aware that this particular way of storing the key (although it is quite secure since no intruder will reach it) should be a temporary solution to the matter. The reason is that the ink fades over time and you may simply cease to recognize the characters that you would need to enter.
Encrypted USB flash drives
These portable devices provide a convenient and reliable means of storing sensitive data and files of any kind. They combine ease of use with a high level of security, making them a popular option for people who value the privacy of their information.
Multi-factor authentication (2FA)
Using this technique, it offers two-step security by requiring users to provide two or more types of identification before accessing an account.

How exactly does it work?
MFA empowers users to choose from a wide array of identification methods. These methods may include:
- Things only YOU can know (password or PIN): this is based on your awareness of sensitive information. The user is required to enter either PIN or a password.
- Devices you have (mobile phone, USB dongle or smart card): this one is relying on your possession of a gadget that generates single-use authentication codes.
- Biometrics (fingerprint, face recognition): this method uses biometric data to confirm the user’s identity.
- Your location: this one implies checking the user’s location via GPS or IP.
Why is MFA so important?
- An additional layer of security: MFA brings an extra layer of protection, so that even if your password is revealed to attackers.
- Phishing protection: even if you mistakenly visit a phishing website and enter your password, attackers will still not be able to access your account without requiring additional forms of authentication.
- Device loss prevention: once your device is lost or stolen, crooks won’t be able to gain access without a 2FA.
Multisignature / Multisig (shared wallet)
Multisig is a concept that supplements security of the storage as well as how you manage your digital assets. The basic idea here is that some mission-critical operation (say, a crypto transaction) requires the validation or signature of multiple participants. Let’s take a look at why this is essential and how it works.
Perfoming multisig implies that the private key(-s) is shared between different participants or devices. Then to complete the transaction, you would need to obtain signatures from a certain number of people as defined by the terms of the contract.
This can be particularly useful in the following cases:
- Commercial transactions: in a business environment where contracts and transactions remain vital, multi-signature helps to ensure consistency of transactions and prevent unilateral actions.
- Asset management: for crypto holders this indicates that administration of assets may require the signatures of multiple participants, rendering them more secure from being thieved.
- Blockchain voting: as for such systems, multisig can be used to guarantee the integrity and robustness of the vote.
Benefits of multisig
- Higher security: multisig makes your system more resistant to hacking, as attackers will likely want multiple keys, not just one.
- Single-party decision prevention: major solutions or operations may require the agreement of several parties, which helps prevent rash actions.
- Integration into smart contracts: Shared wallet can be easily integrated into smart contracts on any blockchain, thus making it possible to control access to your funds.
Conclusion
We have covered a handful of key aspects of securing digital assets. Ranging from hardware wallets and encrypted USB drives to multi-factor authentication and multisig, each of these methods delivers an additional layer of protection in a world of ever increasing value and vulnerability for digital assets and data.
Staying safe in the digital age requires proactive efforts and constantly updating strategies. Keep in mind that there is no one-size-fits-all solution for all scenarios, so a fusion of different methods and techniques may actually be the best approach. The key is to stay vigilant, keep up with the latest cybersecurity trends, and always make it a priority to protect your digital assets.
